Cyber Security: The only approach
The acquisition of Channel Island technology business C5 Alliance by BDO in Jersey earlier this year created a powerful unified firm spanning consultancy, strategy, digital technology and managed services. Scott Nursten, Chief Technology Officer at C5 Alliance, takes a detailed look at the ongoing challenge of cyber security and how it requires a continuously evolving approach to combat it effectively.
The cyber threat is a pervasive one and will only increase. Threats are becoming more innovative and adaptable. There is a very simple fact that applies to all businesses today: you will, at some point, be attacked. And if it’s not you, it will be someone in your supply chain which will also affect and impact your business.
The current state
The global outlook has shifted focus towards how we respond to attacks, when they occur. It is, however, vital that we maintain a robust defence and minimise our exposure to opportunistic attackers. Security experts are literally engaged in an arms race; however the problem with the current approach is that we never know what tomorrow’s threat will look like and we can only base our defences on yesterday’s attacks. Therefore, a standard approach has been to look at the most recent areas of weakness and simply try to patch them.
The secret to future cyber defence is taking a proactive approach
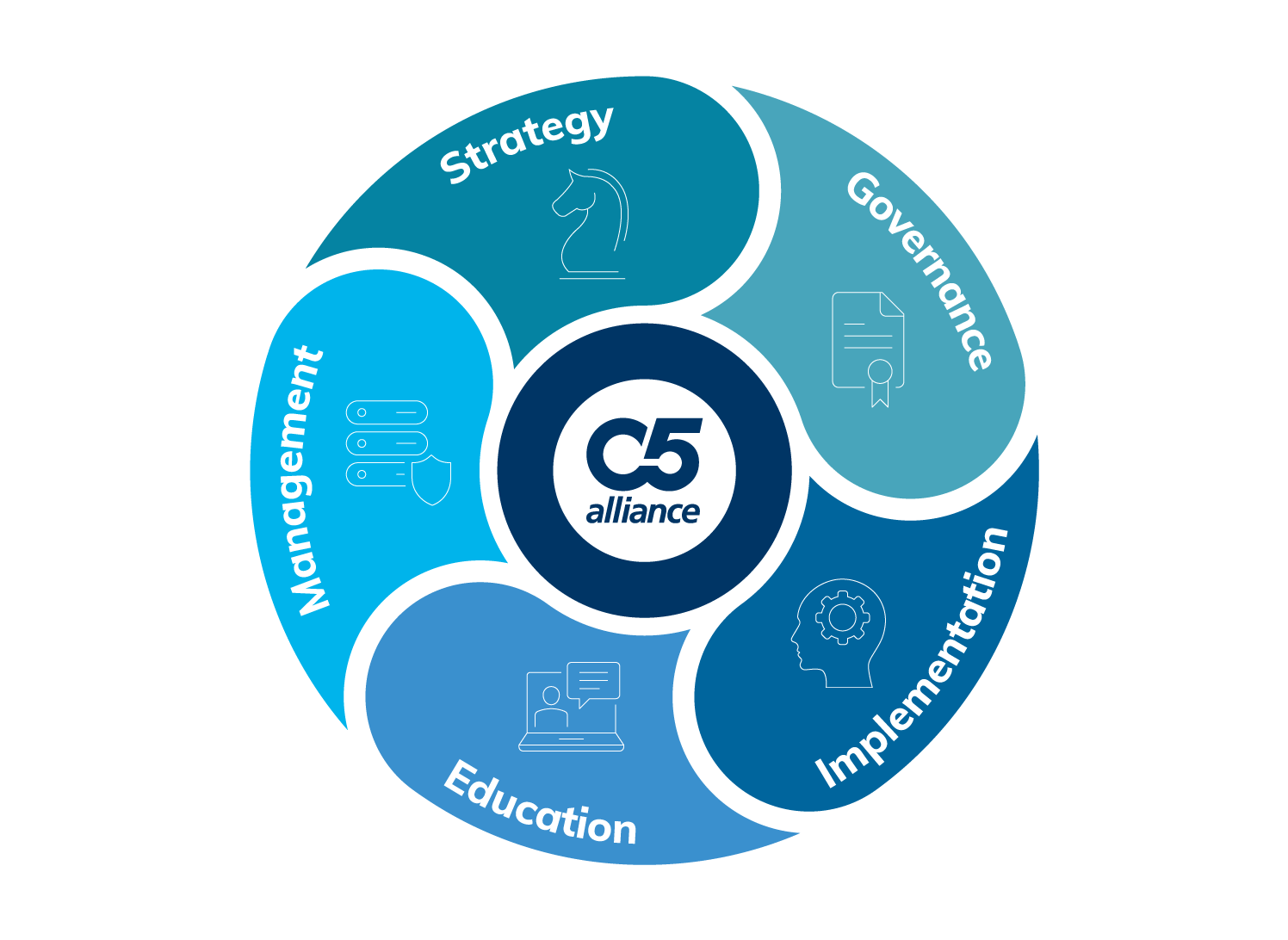
It’s great to see the UK government taking a proactive approach through the National Cyber Security Centre (NCSC). Their approach mirrors the approach we take at C5, in that they see the flow from initial strategy right the way through to ongoing monitoring and management must be run as a lifecycle: security is a virtuous circle with no beginning and no end.
We are aligned also with the four key steps in the stated mission of the NCSC, to make the UK the safest place to live and work online:
- Understand the threat
- Reduce the impact
- Respond to incidents when compromised
- Nurture capability and talent in the cyber security space
This is echoed by both the States of Jersey and Guernsey. Jersey has issued its Cyber Security Vision 2020, to ‘make Jersey a safer place to live and to do business’, while Guernsey is rapidly adopting the NCSC framework.
The key to all of these work programs is that they require effort and understanding on both an individual level and a business level. These aims cannot be achieved in isolation therefore it’s all of our jobs to embrace this movement so we can all understand how best to respond to threats.
How we respond to evolving threats
Unfortunately, most businesses go straight for products with vendors promising the earth. Whilst there are incredible products and platforms out there, if you simply put a product in place, how do you know it’s been deployed properly? What about governance? Who has the keys to the kingdom? Then there is the endless quagmire of compliance and regulation to consider.
There really is only one approach effective in cyber security today and this is the lifecycle approach that the NCSC is also advocating.
Of these steps, strategy, governance and education are the key to ensuring that the implementation and management phases happen effectively – they are the glue in the process. Without these, we see the continuation of specific product deployments resulting in the scariest outcome possible: a false sense of security.
Strategy, planning and advisory
Security strategies and programs should be closely aligned with your business goals. Your strategy should reflect the business needs and ensure your security delivery increases efficiency, protects data and users while maximising your investment. The best advisory, planning and strategy services will always help you strike the right balance when considering all these aspects as well as offering you expert knowledge.
Top tip: Choose a provider that really understands your business. Go for specialists with industry-specific knowledge and experience.
Governance, risk and compliance
Any effective security program requires security experts who can provide guidance and recommendations to help you make informed decisions. You need to address gaps, understand your level of risk and be able to effectively allocate resources to better protect your organisation, all while considering your compliance obligations.
Top tip: Your entire board must be bought-in to this phase. This is essential to protect against weak decision making. It also provides the executive level understanding to make the rest of the phases run smoothly.
Implementation
This is the part everyone wants to jump ahead to as it’s where the fun happens. Unboxing and deploying cutting edge technologies is what most IT professionals live for. The key to good implementation, however, is in deploying usable solutions that fit your business goals and interoperate seamlessly.
This requires a diverse skillset and significant expertise in testing and deploying solutions from your chosen technology partners.
Top tip: Make sure your ongoing monitoring and management architecture is crystal clear before you start implementation. How you’re going to run it is just as, if not more important, than how it is deployed.
Education and awareness
People are often the weakest link in many businesses. Cyber security awareness training for all staff is a vital part of any organisation’s defences against cybercrime. Providing in-depth and interactive staff training is the best way to mitigate the risk of a cyber security breach. In today’s data-rich environments, every member of staff is a potential attack vector.
Top tip: Engage a training partner who can provide a continuous program. Remember security knowledge must evolve as fast as the threat.
Management
Resist the urge to go with the lowest cost provider if they don’t understand your business and can’t help you achieve your strategic goals. Remember the average breach costs businesses almost £1million. Going with the cheapest solution today may prove to be a false economy. It’s vital that your managed service factors in:
- Monitoring
- Event correlation and management
- Device and endpoint management
- Incident management and response
- Continuous vulnerability assessment
- 24×7 response
Top tip: Make sure the provider you choose works well with your team and is a natural extension of your security capability. You should be thinking about a long-term trusted partnership.
Taking your business out of cyber criminals’ cross-hairs
No solution will ever be 100% secure and the threats continue to evolve. This however, doesn’t change the fact that attackers always go for the easiest targets. Embracing a lifecycle approach to security means you’re covering every base possible and there will always be an easier target than you.
If you would like to discuss your cyber security requirements, please get in touch with Richard Welsh, Chief Commercial Officer, C5 Alliance – Richard.welsh@c5alliance.com